Cyber incidents are unwanted or unexpected events that compromise the confidentiality, integrity, or availability of digital systems or information. These events can include targeted attacks — like ransomware or phishing — as well as accidental errors, system failures, or misconfigurations. Cyber incidents pose a serious threat to operational continuity, reputation, and security for any organization.
Types of cyber incidents
Cyber incidents can take many forms, including:
- Ransomware attacks: malicious software encrypts files or systems and demands a ransom for access.
- Phishing and social engineering: deceptive techniques trick users into revealing sensitive data or taking harmful actions.
- Data breaches: confidential information is leaked, stolen, or exposed — intentionally or accidentally.
- DDoS attacks: services are disrupted by overwhelming systems with traffic.
- Exploits and vulnerabilities: attackers exploit unpatched software or misconfigurations.
- Insider threats: internal users (malicious or careless) compromise security.
- Credential stuffing: attackers use leaked passwords to access systems through reused credentials.
Even minor incidents can reveal critical security gaps if not addressed properly.
The impact of cyber incidents
Cyber incidents can result in:
- Operational disruption: business processes halt, and services become unavailable.
- Financial loss: recovery costs, fines (e.g., under GDPR), legal fees, and lost revenue.
- Reputational damage: loss of trust among clients, partners, or investors.
- Regulatory consequences: mandatory reporting to authorities under laws like NIS2 or DORA.
- Supply chain risks: an incident at a vendor can directly affect your operations.
Rapid detection, response, and recovery are vital for effective cyber risk management.
Cyber incidents and supply chain vulnerabilities
In today’s interconnected world, cyber incidents often affect more than one organization. Examples include:
- A data breach at your HR service provider exposing employee records.
- A compromised software vendor distributing malware through updates.
- A ransomware incident at a logistics partner delaying your deliveries.
This is why organizations must monitor not just their internal systems, but also their extended digital ecosystem. Regulations like NIS2 and DORA reinforce this requirement.
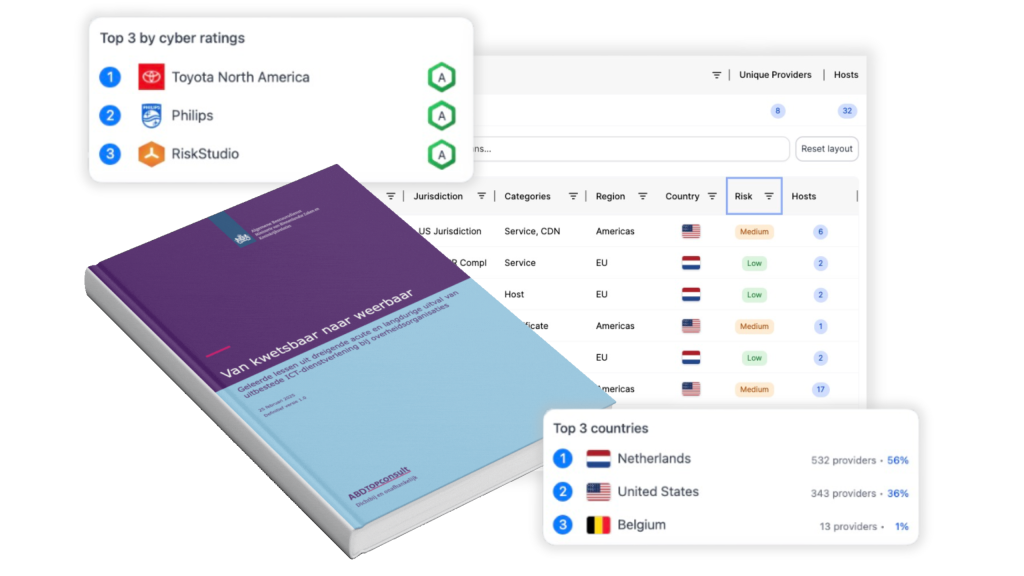
How RiskStudio helps detect and respond to cyber incidents
RiskStudio provides continuous monitoring of your supply chain for signs of cyber incidents — including breaches, ransomware, exposed credentials, and vulnerabilities. You receive real-time alerts when a supplier or subcontractor is affected.
The platform helps you link incidents to critical business areas, assess supplier history, and organize your response. Whether you’re dealing with an incident report, an audit, or a risk evaluation — RiskStudio gives you the tools to act quickly and confidently.