A cyber footprint is the collection of digital traces an organization or individual leaves behind on the internet and in IT environments. This includes domains, email servers, cloud assets, IP addresses, software versions, exposed ports, and leaked credentials. Your cyber footprint reflects your digital presence — and for cybercriminals, it can serve as a roadmap to attack. The larger or less managed your footprint is, the greater your exposure to threats.
Types of cyber footprints: active and passive
Cyber footprints are typically divided into:
- Active footprint: data you intentionally publish or deploy, such as websites, APIs, cloud services, and social media accounts.
- Passive footprint: data collected without explicit action, such as IP logs, cookies, metadata, or leaked credentials from breaches.
For organizations, this footprint often includes forgotten or externally managed assets — also known as shadow IT or orphaned assets — which are especially vulnerable to exploitation.
Why cyber footprint matters in cybersecurity
An unmanaged cyber footprint increases your attack surface. Threat actors use automated tools to scan publicly available data about companies — a process known as reconnaissance. They look for outdated systems, misconfigurations, expired certificates, or open ports.
Leaked credentials or exposed email addresses also enable targeted phishing attacks. Without a clear view of your footprint, it’s nearly impossible to understand what systems are externally exposed and how attackers might use them.
Mapping your cyber footprint is essential for prioritizing vulnerabilities, strengthening asset management, and enforcing consistent security policies — especially across third-party systems.
Cyber footprint in the supply chain
The cyber footprint of your suppliers is just as critical as your own. If a subcontractor unknowingly exposes a vulnerable server online, your organization may also be at risk. High-profile supply chain breaches — like SolarWinds or MOVEit — often begin with an exposed or unpatched asset.
To truly understand your security posture, you need visibility into the full footprint of your digital ecosystem, including third parties and service providers.
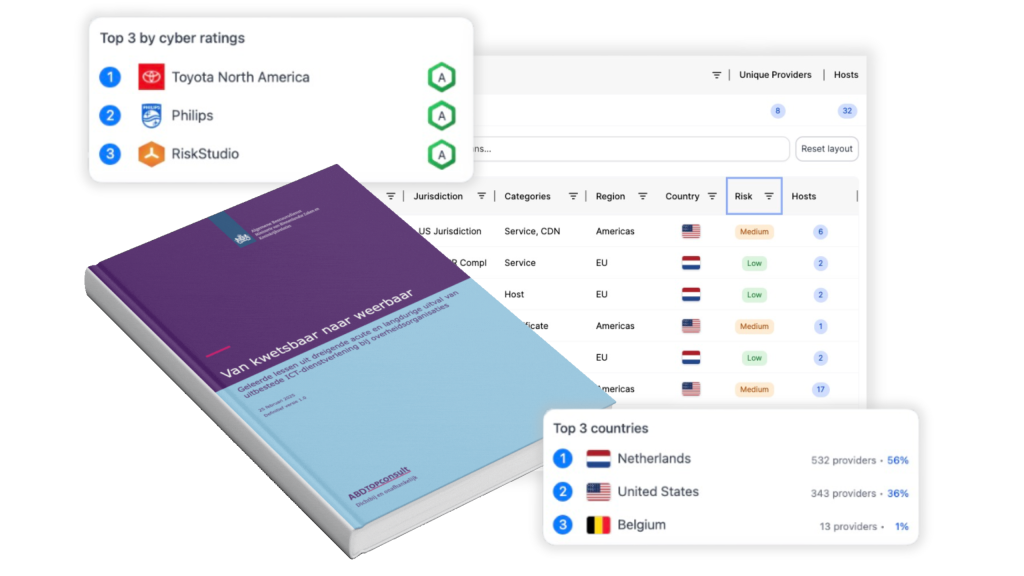
How RiskStudio reveals your cyber footprint
RiskStudio makes your cyber footprint — and that of your suppliers — instantly visible. Through external scanning, we automatically detect publicly accessible IT assets, outdated systems, leaked credentials, and open vulnerabilities.
You get a clear overview of domains, servers, misconfigurations, and other digital risks, enriched with real-time threat intelligence. This insight helps you clean up shadow IT, reduce exposure, and focus your security efforts.
By assessing suppliers based on their cyber footprint, you can make informed decisions, react quickly to new threats, and continuously improve your digital resilience across the entire supply chain.