Cyber exposure refers to the full spectrum of digital risks an organization faces through its IT infrastructure, applications, users, third parties, and business processes. It goes beyond vulnerabilities and looks at how exposed an organization is to potential cyberattacks. In other words: cyber exposure is about how visible, accessible, and vulnerable your digital assets are to attackers.
From vulnerability to exposure
Many confuse cyber exposure with a list of vulnerabilities. But vulnerabilities alone don’t define exposure. Exposure is the intersection of vulnerability and accessibility.
For example:
- An unpatched server hidden in your internal network is a vulnerability.
- The same server exposed to the internet becomes a cyber exposure.
Cyber exposure includes public-facing systems, misconfigured cloud environments, outdated applications, and leaked credentials — especially when these are accessible from the outside.
Why cyber exposure matters
Cybercriminals are constantly scanning for weaknesses in exposed systems. Organizations with high exposure are more likely to suffer ransomware attacks, data breaches, or system compromises.
Managing cyber exposure allows you to:
- Prioritize risk: Not all vulnerabilities are equal — exposure determines urgency.
- Prevent incidents: Reducing external attack surfaces lowers your chances of being targeted.
- Demonstrate resilience: Regulations like NIS2 and DORA expect exposure awareness and control.
- Secure your supply chain: A third party’s exposure becomes your exposure in an interconnected ecosystem.
Third-party exposure: the hidden risk
Today’s organizations rely on countless third parties — cloud providers, software vendors, partners, consultants. Each has its own digital footprint. If a supplier has weak cybersecurity and is exposed online, your organization inherits part of that risk.
Think: vulnerable vendor portals, exposed APIs, or leaked credentials from a partner. Without visibility into supplier exposure, your own defenses are incomplete.
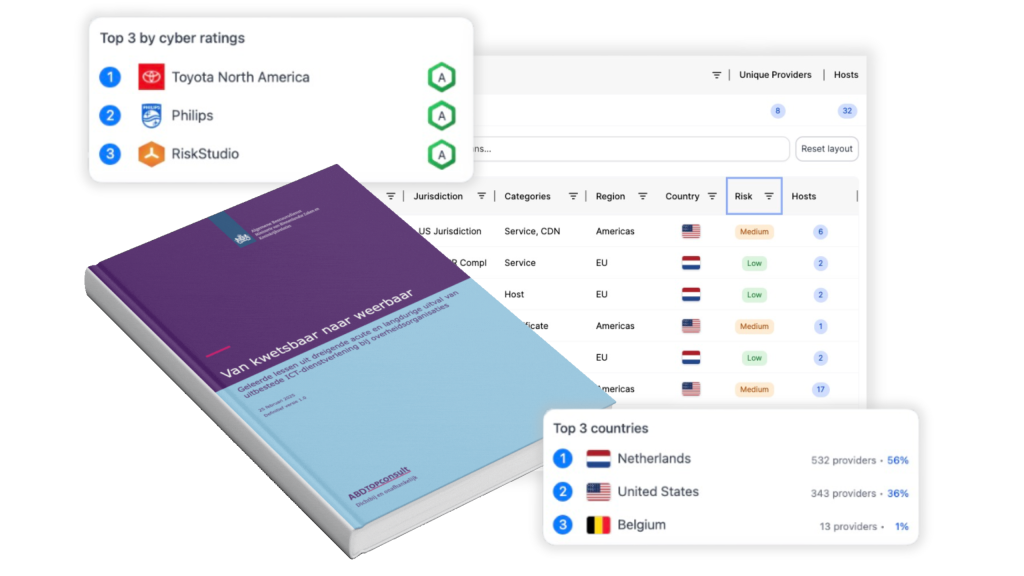
How RiskStudio reveals and manages cyber exposure
RiskStudio transforms cyber exposure into actionable insight. The platform continuously scans the public digital footprint of your organization and its suppliers. You instantly see which systems are exposed, which vulnerabilities exist, and where critical risks arise.
With automated cyber ratings, real-time threat alerts, and prioritized actions, you get a clear picture of exposure across your ecosystem — without lengthy assessments or manual analysis. Assign responsibilities, organize your response, and reduce exposure proactively.
RiskStudio turns cyber exposure from an abstract concept into a central part of your risk and compliance strategy.