MITRE ATT&CK is a public framework that categorizes and describes real-world cyberattack techniques. Developed by the MITRE Corporation, ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) is used globally to understand, detect, and respond to cyber threats. It maps how attackers operate — from gaining access to exfiltrating data.
How does MITRE ATT&CK work?
The ATT&CK framework outlines the full lifecycle of an attack using:
- Tactics – the what (e.g., initial access, persistence, data exfiltration);
- Techniques – the how (e.g., phishing, lateral movement, abuse of valid accounts).
Each technique includes detailed examples, detection tips, and mitigation strategies. MITRE ATT&CK is structured into several matrices:
- Enterprise: for IT environments (Windows, Linux, macOS);
- Mobile: for Android and iOS threats;
- ICS: for industrial control systems.
This structure helps security teams align their defense with real adversary behavior.
Why is MITRE ATT&CK important?
MITRE ATT&CK provides a common reference for:
- SOC teams and threat hunters;
- Red and blue teams;
- Technical risk assessments;
- Maturity benchmarking.
It allows organizations to understand which attacker techniques they can detect or defend against — and which gaps still exist.
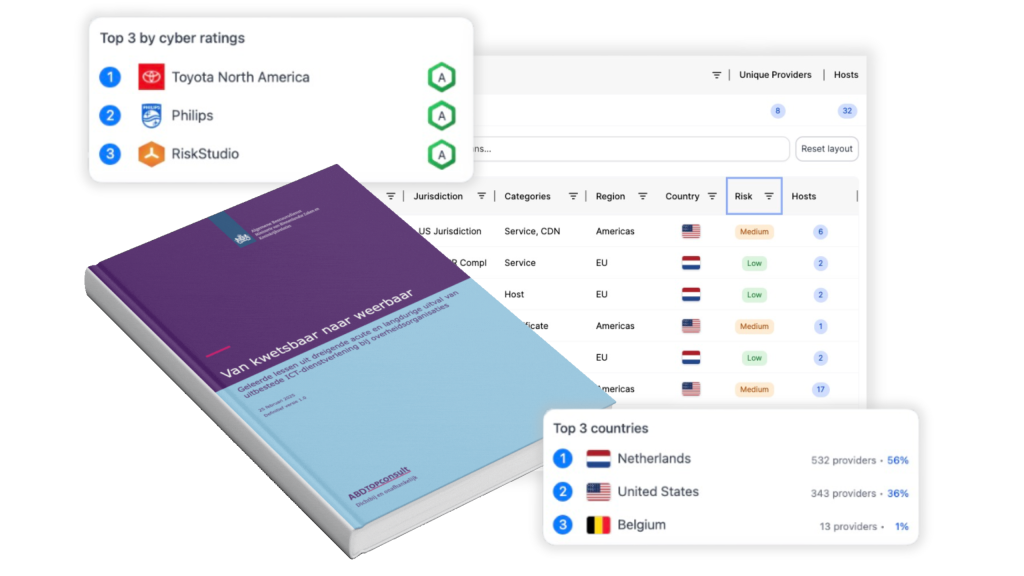
MITRE ATT&CK and RiskStudio
RiskStudio maps vulnerabilities, incidents, and supplier risks to relevant ATT&CK techniques. When a vendor is affected by a ransomware attack or a vulnerability that enables tactics like remote code execution, RiskStudio shows where the threat fits within the ATT&CK framework. This enhances prioritization, incident response, and technical decision-making. RiskStudio turns ATT&CK into a practical tool for supply chain risk management — actionable, clear, and fully integrated.